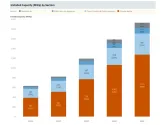
DDoS attacks: Could your bank be the next victim?
Experts reveal how banks can circumvent such attacks.
Banking executives are still reeling from massive Distributed Denial of Service (DDoS) attacks in the last few weeks, the latest being a high-profile attack on five major banks in Russia. Powered by a botnet of hacked IoT devices known as Mirai, the attacks overwhelmed websites with spam traffic so legitimate users couldn’t get through and access the organization’s digital platforms.
Robin Schmitt, head of APAC for security and marketshare at Neustar, said that the Mirai botnet has been used in some of the largest and most disruptive distributed denial of service (DDoS) attacks, including an attack on computer security journalist Brian Krebs's website and the Dyn cyber attack.
While the digital age has brought banks closer to customers, it has also exposed them to its dark underbelly–cybercrime. Banks now have a huge task of making sure that their products are up to speed against highly sophisticated and innovative digital hackers, many of which have launched high-profile security breaches and money laundering schemes in recent months.
The digital space is an added platform for fraudsters to engage in traditional fraud schemes. Mike Shaw, vice president, global market development, LexisNexis Risk Solutions, said that money laundering, enabling the funding of terrorist acts, fraud and banking tax evaders remain real-world risks that banks still face every day. Vulnerabilities to these schemes have only increased with the fluidity of digital transformations.
Today, banks are at risk of ever-evolving phishing and malware, DoS attacks, and unpatched software, among many other forms of attack. According to Sanjay Rohatgi, senior vice president, Asia Pacific and Japan, Symantec, cybercriminals have begun to display a deep understanding of the internal financial systems used by banks. They have learned that banks employ a diverse range of systems and have invested time in finding out how they work and how employees operate them. When coupled with the high level of technical expertise available, these groups now pose a significant threat to any organisation they target.
Asia’s top IT experts observe that banks have been overly focused on delivering the best digital solutions without the equally necessary strategy to secure their banking systems. Schmitt said that banks have to clearly define their cyber security strategy and adequately assess security implantation. He added that so far, banks are still struggling to keep up despite their many efforts of keeping cyber attacks at bay.
Tim Liu, chief technology officer, Hillstone Networks added that the security levels of new areas such as mobile and online support and integration of payment capabilities are less well understood by banks, but the heavy usage of these platforms should lead banks to increase focus and investment on online and digital security.
Cybercrime hotspot
Schmitt said that with the rise of IoT devices, DDoS attacks will definitely grow in scale and frequency, thereby exposing organizations and their customers to risk. Due to the financial gain and the wealth of data derived from banks, the financial industry remains the one of the most targeted areas for fraudsters and therefore one of the most vulnerable.
“Valuable data such as account/credit status, financial transactions, and private consumer information – a goldmine for criminals - is now potentially exposed in an open environment, as services are conducted over the internet and often requiring collaboration among multiple parties,” said David Jones, head of payments & banking at Irdeto. According to Jones, the three most pertinent security challenges affecting banks are protecting data, protecting the application program interface (API), and ensuring that the application development process follows the best security practices.
Ng Sheung Chi, senior security consulting manager, Identity and Data Protection (IDP), APAC, Gemalto, said that because financial technology is increasingly embedded into traditional banking and financial services banks nowadays, banks are dealing with more personal information on top of the financial information they traditionally handle. Ng added that banks now have access to a huge amount of a user’s personal information, like locations, photos, biometrics, and network of friends. This sudden surge of new information must be protected by banks, therefore requiring them to increase security methods that were previously not there.
“New modes of banking such as mobile payment, mobile retail, or mobile ebanking services need to be sufficiently secured against cybersecurity risks taking advantage of the Wifi, Bluetooth, or Near-Field Communications connectivity,” said Ryan Flores, senior manager, Forward-Looking Threat Research, Trend Micro, Asia Pacific. Flores added that banks must address hacking activities on every front possible – from mobile apps to backend servers to ATMs.
CISOs in the finance industry are also faced with all of these challenges, said Itay Yanovski, founder and senior vice president, strategy, CyberInt. According to him, CISOs need to support the business growth and change while keeping the business safe from the growing cyber threat. For the banks, CISOs have now become business enablers as opposed to merely IT security managers, requiring them to think out of the box and proactively mitigate threats before they become cyber incidents.
No silver bullet
Banks on the lookout for a one-size-fits-all strategy against cyberfraud will only be disappointed. The fast-evolving nature of technology requires banks and CISOs to be vigilant in keeping their systems seamless and up-to-date. IT experts agree that a more holistic approach must be drawn up and regularly updated to cover all the possible entry points for hackers.
“Banks should focus on the business risk associated with all their channels and assets, allowing them to prioritize and rationalize the resource allocation and enhance their security posture. In most cases, transaction monitoring and fraud detection are pretty high in the list,” Yanovski said.
Security may also be looked at through a layered-approach, one wherein different controls are used at different points in a transaction process. Gemalto's Ng said that this approach is characterised by protecting the devices, authenticating the user, monitoring for anomalous behaviour, and encrypting the data. This range of solutions, according to Jones, must have policies that can secure exchange with back-office servers that house sensitive business and consumer data.
“Vulnerability scanning tools can be used to scan websites and mobile apps. On the application level, there is a need to think about security in operating the application, such as protecting websites with WAF appliance or DDoS service, or preventing mobile apps from being laced with malware and delivered to the customer. Some mobile apps use out of band authentication such as SMS and check operating environments for suspicious apps and processes,” added Hillstone Network's Liu.
As there is no single strategy, banks must also recognize that a single infrastructure is more prone to risk than a distributed one. Neustar's Schmitt stressed that financial institutions should separate their DNS, e-commerce, payment gateways and VPNs to prevent widespread damage once they are hit with a DDoS attack.
“If for instance DNS is under attack but VPN is on a different circuit (either real or virtual), employees have backdoor access to email and other functions. Because private and public-facing systems are segregated, at the time of the attack business doesn’t grind to a complete halt,” Schmitt said.
While banks are at it, Symantec's Rohatgi said that they must also educate their clients who are at the receiving end of all these risks. He added that security simulation built into security awareness training can drive lasting change in employees by educating them beyond just “how” attacks are carried out, and covers “why” they should look out for warning signs.
Circumventing DDoS attacks
While DDoS attacks in other industries are mostly hacktivist in nature, Trend Micro's Flores says that DDoS hackers in the banking industry are definitely financially motivated. DDoS attacks remain one of the most challenging attacks in the financial industry due to their diversity, growth speed, and the ease with which they are launched.
“The nature of the attacks is that they are simple to deploy and do not require much investment in highly sophisticated technology. This means hackers will always keep trying to inundate the banks with DDoS attacks. In addition, should hackers hire volunteers or normal users to flood the banks’ servers with nonstop requests, such traffic would be harder to detect and block as banks will have a difficult time discerning if it’s legitimate or malicious,” Flores added.
DDoS attacks have also become elusive, making it even more difficult for bankers to detect and mitigate in time. Schmitt said that hackers deploy the attacks in concert with other activities to distract and disrupt target responsiveness. This kind of attack is known as “smokescreen”, which is meant to confuse and misdirect organizations from the primary objective of the assault. One such assault is data theft, which takes the form of malware or ransomware activation.
“As the manpower or IT professionals are directed to resolve the DDoS attack, they potentially leave the rest of the system unmonitored. This can create a ‘quiet period’ for the hackers to attack other parts of the system.To prevent a DDoS attack from happening, the banks must work with their telcos to monitor such torrent of traffic. Once detected – say a device keeps sending requests to the system, the telcos can help the bank block the particular device, cutting off the traffic and preventing a potential DDoS attack,” said Ng.
Rohatgi added that Symantec has outlined some steps that banks can take in mitigating DDoS attacks. Bank must begin by preparing a thorough gameplan, which includes having an agreement with a mitigation service. They can then create a DDoS playbook, which includes a communication strategy for clients, and finally, banks should make sure that they are covered with cyber insurance.
In photo (from left to right): Tim Liu of Hillstone Networks, Sanjay Rohatgi of Symantec, Ryan Flores of TrendMicro, Robin Schmitt of Neustar, Ng Sheung Chi of Gemalto, Itay Yanovski of Cyberint, David Jones of Irdeto















 Advertise
Advertise